Complete Guide to Network Security Groups in Azure VNet
Network Security Groups (NSGs) are a critical component in Azure’s network security model. They act as virtual firewalls, controlling inbound and outbound traffic to Azure resources. This guide will walk you through everything you need to know about NSGs, from basic concepts to advanced configurations.
What are Network Security Groups?
Network Security Groups are virtual firewall rules that filter network traffic to and from Azure resources in a Virtual Network. They provide:
- Granular traffic control
- Enhanced network security
- Flexible rule configuration
- Protection at subnet and network interface levels
Key Components of Azure Network Security Groups
1. Security Rules
Each NSG contains multiple security rules. These rules define the allowed or denied traffic. Each rule has properties like name, priority, source, destination, port, and protocol.
- Inbound rules
- Outbound rules
- Default security rules
- Custom security rules
2. Rule Priority
Rules are processed in priority order, with lower numbers processed before higher numbers. Once traffic matches a rule, processing stops
- Lower numbers = higher priority
- Rules processed in order
- First matching rule applies
3. Rule Attributes
You can specify any IP address, CIDR block, service tag, or application security group as the source or destination.Rules can be defined for specific ports and protocols, allowing for granular control over network traffic
- Name
- Priority
- Source/Destination
- Protocol
- Direction
- Action (Allow/Deny)
- Port range
How NSGs Work: Technical Deep Dive
Traffic Filtering Process
- Inbound traffic evaluation
- Rule matching
- Permit or deny decision
- Logging (optional)
Default Security Rules
Azure automatically creates default rules:
- Allow inbound VNet traffic
- Allow Azure load balancer traffic
- Block all external inbound traffic
- Allow all outbound traffic
Practical Implementation Strategies
NSG Configuration Best Practices
- Principle of Least Privilege
- Restrict access to minimum required
- Explicitly define allowed traffic
- Deny by default
- Granular Rule Design
- Use specific IP ranges
- Limit port exposures
- Regularly audit rules
- Hierarchical Protection
- Apply NSGs at subnet level
- Add interface-level NSGs for precision
- Use service tags for simplified management
Advanced NSG Techniques
1. Service Tags
Predefined IP address categories:
InternetAzureCloudStorageSQL- Region-specific tags
2. Application Security Groups
- Logical grouping of VMs
- Simplified NSG rule management
- Improve network segmentation
3. NSG Flow Logs
- Capture traffic details
- Enable comprehensive monitoring
- Integrate with Azure Network Watcher
- Support forensic analysis
How to create Network Security Group in Azure?
Option- 1 Via Azure Portal
Step 1: Sign In and Navigate
- Open Azure Portal (portal.azure.com)
- Log in with your Azure credentials
- Click on “Create a resource” or the plus (+) icon
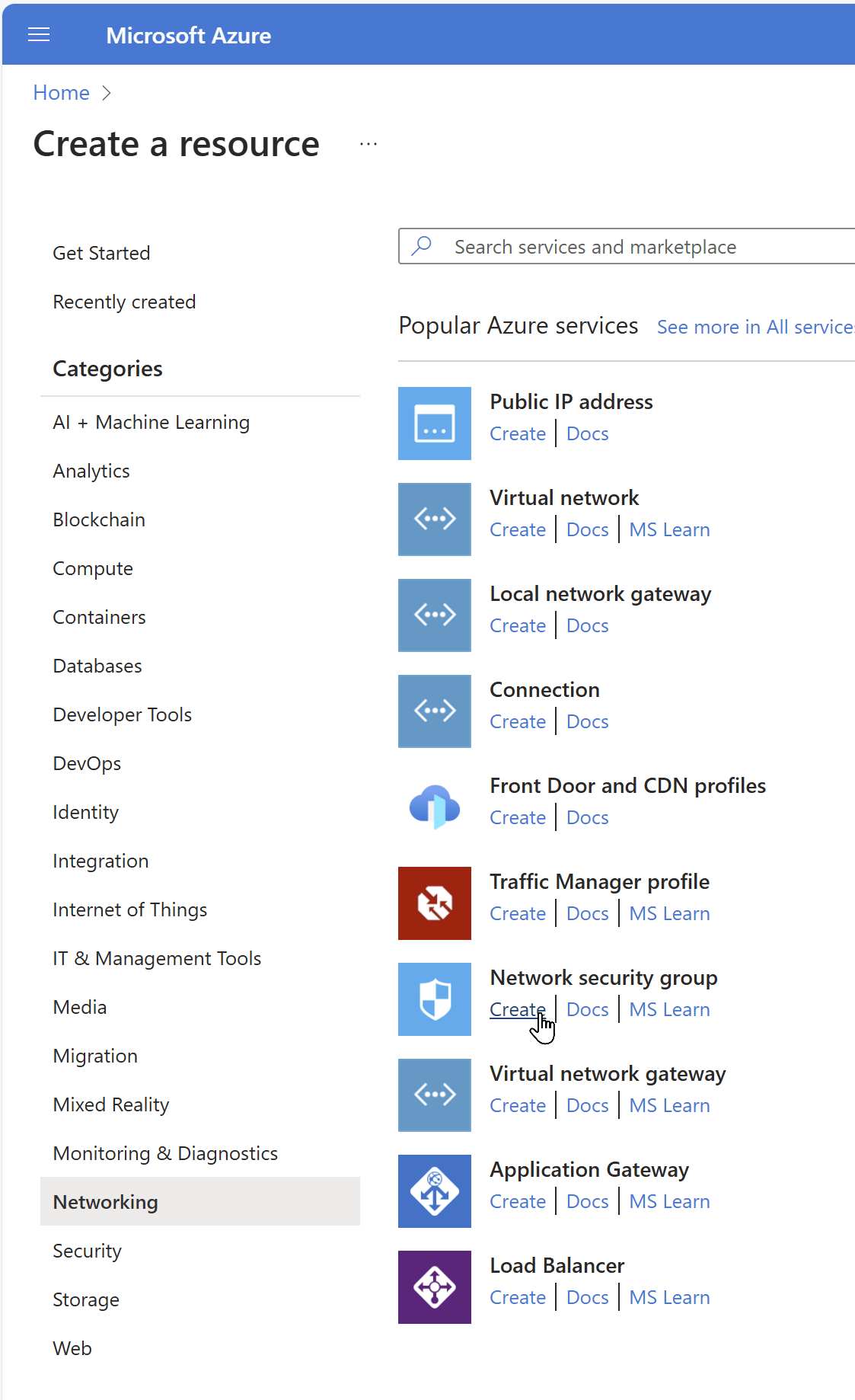
Step 2: Search and Select Network Security Group
- In the search bar, type “Network Security Group”
- Select “Network Security Group” from the results
- Click “Create”
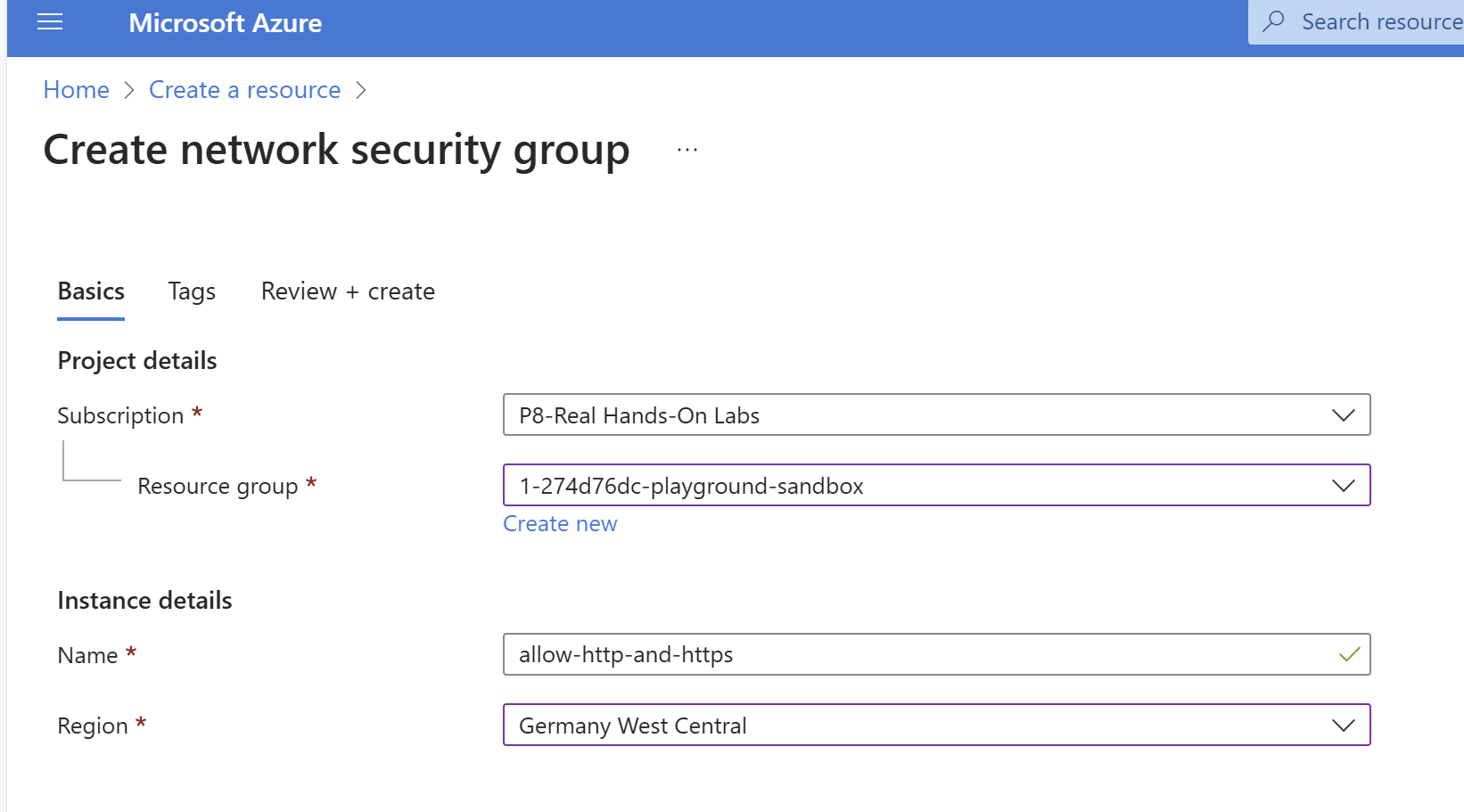
Step 3: Basics Configuration
- Subscription
- Select your active Azure subscription
- Resource Group
- Choose existing or create a new resource group
- Name
- Enter a descriptive name for your NSG (i usually give the intent or purpose of the security group like allow-http-and-https, it is easier to understand what it does with only looking the name)
- Use naming conventions (e.g., NSG-WebServers-Prod)
- Region
- Select the Azure region where you want to deploy the NSG
Step 4: Tags (Optional)
- Add key-value pairs for resource management
- Helpful for:
- Cost tracking
- Resource organization
- Compliance requirements
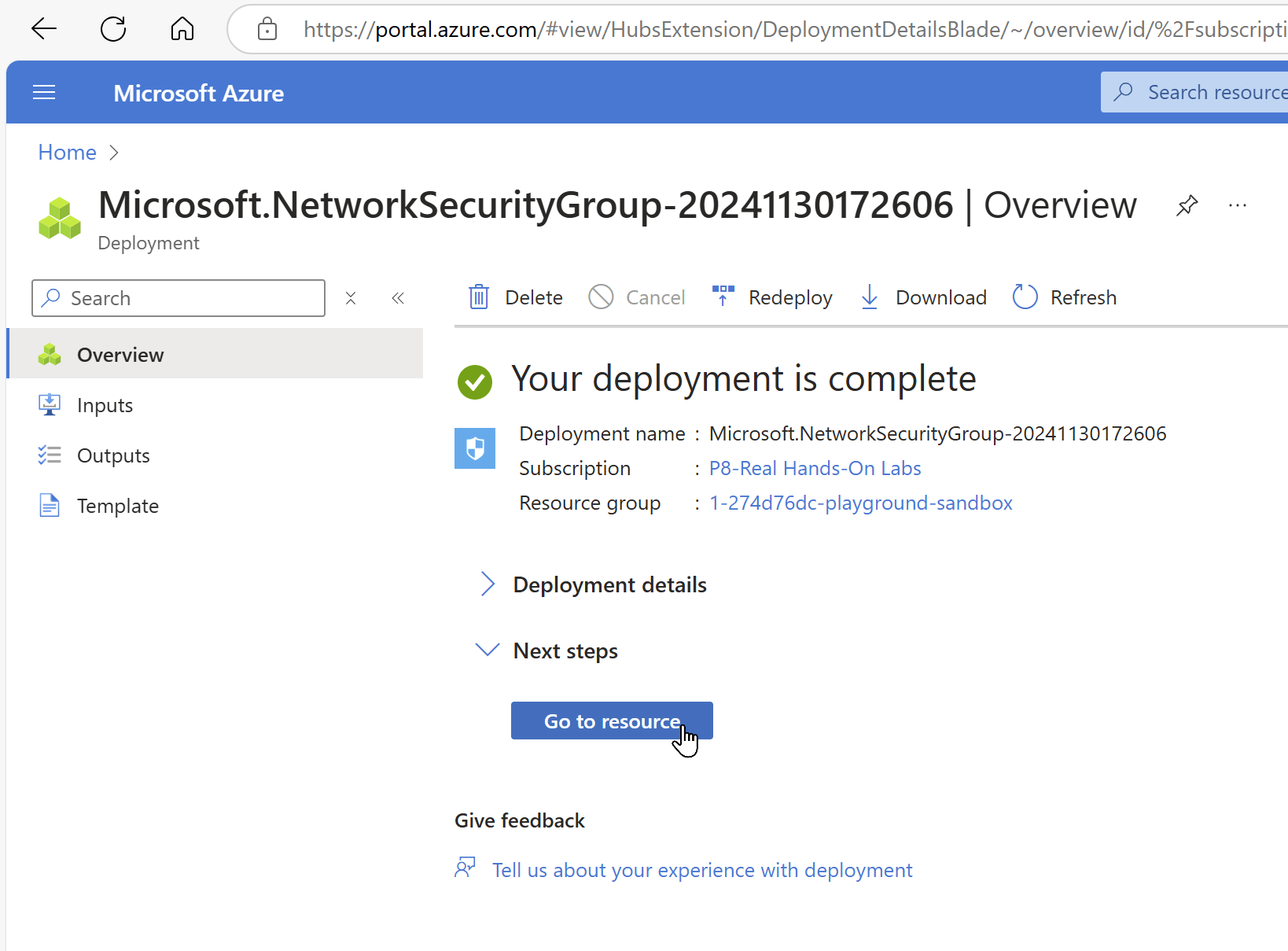
Step 5: Review and Create
- Click “Review + Create”
- Validate configuration
- Click “Create”
Step 6: Post-Creation Configuration
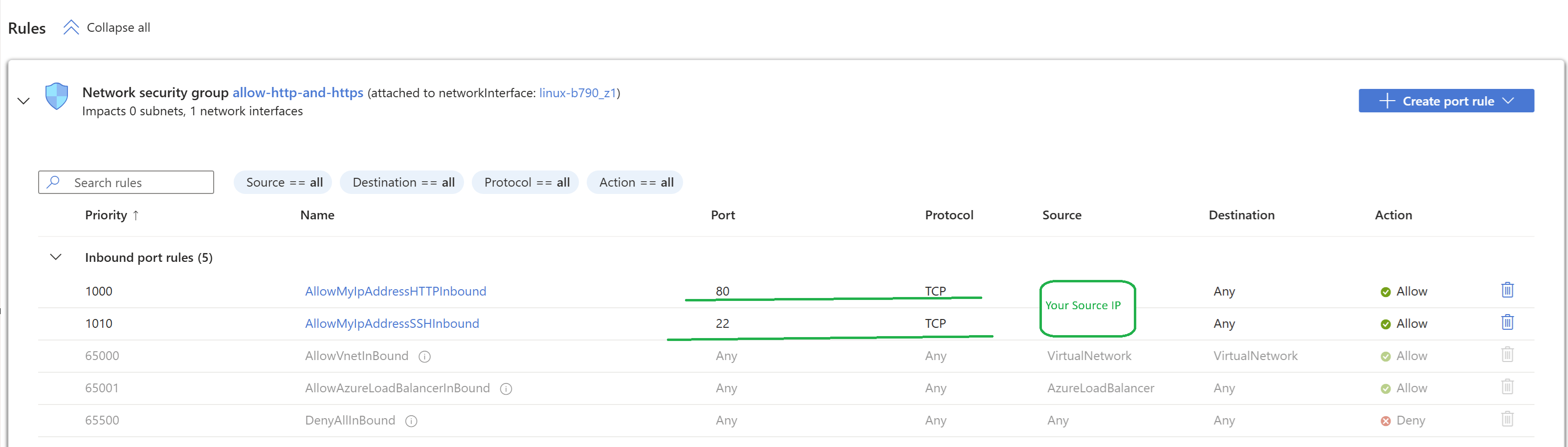
Add Inbound Security Rules
- Open the newly created NSG
- Select “Inbound security rules”
- Click “+ Add”
- Configure rule parameters:
- Name
- Priority
- Source
- Source port ranges
- Destination
- Destination port ranges
- Protocol
- Action (Allow/Deny)
Here i have created 2 new Inbound rules over top of default rules; allowed communication from my local IP addresses to reach via SSH and HTTP.
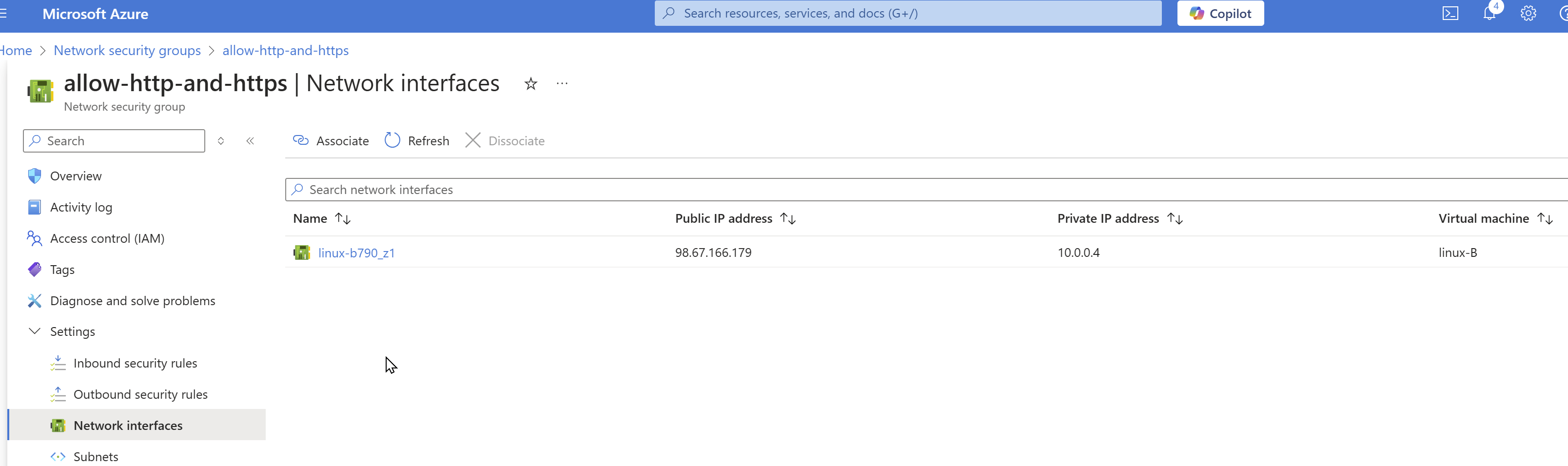
Associate with Subnet or Network Interface
- Go to “Subnets” or “Network interfaces”
- Click “Associate”
- Select target VNet or network interface
I have created a VNET and Linux machine in the same VNET, while creating Linux machine associated Network Security Group with VM but you can also do it later
Option- 2 Via Azure CLI
Hands-On NSG Creation (Azure CLI Example)
# Create Network Security Group
az network nsg create \
--resource-group MyResourceGroup \
--name MyNetworkSecurityGroup
# Add custom inbound security rule Allow SSH
az network nsg rule create \
--resource-group MyResourceGroup \
--nsg-name MyNetworkSecurityGroup \
--name AllowSSH \
--protocol Tcp \
--direction Inbound \
--priority 1000 \
--source-address-prefix '*' \
--source-port-range '*' \
--destination-address-prefix '*' \
--destination-port-range 22 \
--access Allow
# Add custom inbound security rule Allow HTTP
az network nsg rule create \
--resource-group MyResourceGroup \
--nsg-name MyNetworkSecurityGroup \
--name AllowSSH \
--protocol Tcp \
--direction Inbound \
--priority 1010 \
--source-address-prefix '*' \
--source-port-range '*' \
--destination-address-prefix '*' \
--destination-port-range 80 \
--access AllowCommon NSG Scenarios
Scenario 1: Web Application Protection
- Block external SQL access
- Allow HTTP/HTTPS
- Restrict management ports
- Implement IP whitelisting (if you are going to open your resources to internet, it is always good practice to limit where end users or clients are going to connect, opening sensitive ports/protocols without much security in front of them can cause vulnerable and risks in your workloads)
Scenario 2: Multi-Tier Application
- Isolate web, application, database tiers
- Control inter-tier communication
- Implement strict access controls
Monitoring and Troubleshooting
Diagnostic Tools
- Azure Network Watcher
- NSG Flow Logs
- Diagnostic Settings
- Azure Security Center
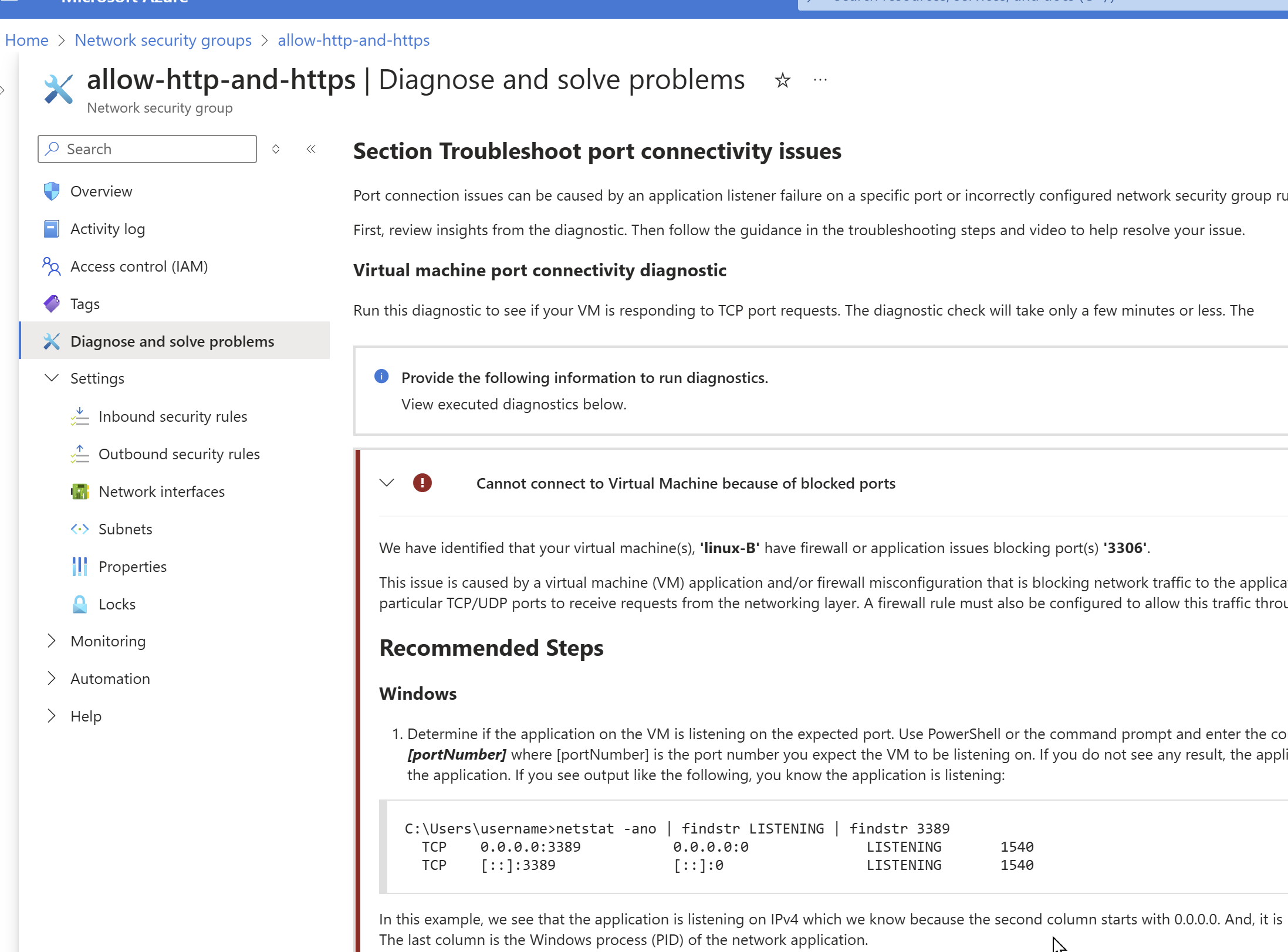
If there are network connectivity issues happening and if you cannot identify the issue easily then i highly recommend Diagnostic section in the NSG, it can provide clear guidance on the problem resolution.
Troubleshooting Checklist
- Verify rule configurations
- Check rule priorities
- Validate service tags
- Review effective security rules
- Use packet capture for deep analysis
Security Recommendations
- Regular NSG Audits
- Quarterly review
- Remove obsolete rules
- Update according to infrastructure changes
- Implement Zero Trust
- Strict access controls
- Micro-segmentation
- Continuous verification
- Enable Logging
- Capture all traffic patterns
- Set up alerts
- Integrate with SIEM systems
Performance Considerations
- Minimal performance overhead
- Stateful inspection
- Negligible latency impact
- Scalable design
Common Mistakes to Avoid
- Over-permissive rules
- Ignoring default rules
- Lack of regular audits
- Complex, unmanageable rule sets
- Neglecting logging
Conclusion
Network Security Groups are a powerful tool for securing your Azure environment. By understanding and properly configuring NSGs, you can significantly enhance the security of your Azure resources. Follow the best practices and regularly review your security rules to maintain a robust security posture.
Secure your cloud. Master Azure NSGs today!
FAQ Section
Q1: Are NSGs free?
No cost for NSGs, but associated resources like Network Watcher have charges.
Q2: How many rules can an NSG have?
Up to 1000 rules per NSG.
Q3: Can NSGs span multiple VNets?
No, NSGs are specific to a VNet or subnet.
Q4: How do I diagnose NSG issues?
Use Azure Network Watcher and effective security rules view.
Q5: Can I use NSGs with PaaS services?
Yes, using service endpoints and private links.